Last Updated: 08/02/2021
Introduction
I have been asked a few times now what to do if you think an Office365 account is compromised. My answer is always to kick off your Incident Response process and involve a forensic investigator. However, it never hurts to have an idea of some of the activities you can perform to start a base level of containment. I have put this guide together so you have a few go-to activities if you suspect an account might be behaving suspiciously.
General order of the steps to take would be:
- Disable User Account.
- Revoke any admin access or special/privileged permissions.
- Sign Out of all sessions and revoke tokens (See below for steps).
- Remove any suspicious forwarding addresses set at the mailbox level (Info on Forwarding Addresses here).
- Remove any suspicious inbox level rules, set within the mailbox. Configurable in OWA.
- Switch Mailbox to Legal Hold to preserve content (See here for info).
- Enable Mailbox Auditing (Click here for the Microsoft guide to enable Mailbox Auditing, which is disabled by default).
- Check Email and SharePoint permissions and rules (Please note that SharePoint sites have there own system for permissions).
- Reset Password (Ensure that this is synced across if using AD Connect) DONT SEND THE PASSWORD VIA EMAIL.
- Enable or Reset MFA factors and enrol with the User to ensure it is only their device being enrolled.
- Re-enable the user account in Azure AD.
- Monitor Activity on the Account (Check Mailbox Audit logs).
- Introduce permissions and access.
Sign out of ALL sessions
First thing to understand is that when a user is logged into Office365 they are consuming multiple services which use tokens for authentication. Tokens are used to prevent users from logging in every time they click on a different service (Exchange, SharePoint, OneDrive ect.). These tokens leave users logged in effectively. If a user’s machine is compromised by Malware then chances are they can leverage these tokens to access Office365 services for that user. In this case, we need to kill the sessions and revoke the tokens being used to ensure that bad actors are locked out.
We can initiate a sign out of a user that will sign the user out of any active session, this can be done from the GUI Office365 Admin portal.
Within the Admin Center if we locate the compromised user and navigate to the OneDrive tab we can initiate a sign out, this will sign the users out from all active sessions within Office365 (I am not sure why this is under OneDrive, but it should sign users out of everything Microsoft based). Prior to this it is recommended to block user sign in, post this step would be to change the password of the user.
Using PowerShell to revoke tokens from Azure AD
However, if Azure AD is being used for more than just Microsoft (Single Sign On for Azure AD Applications) then this sign out method above will not work for those additional applications. In order to kill the sessions and revoke the tokens we will need to use PowerShell. If you haven’t done so already then install the AzureAD PowerShell module, you can run the following command without Admin Access to install the module to your local profile:
Install-Module AzureAD -Scope CurrentUser
Once you have the module installed, connect to Azure AD using your credentials. Make sure you have User Management Administrator Access to run the Revoke Command. You can log into Azure AD by running the following command and entering in your credentials:
Connect-AzureAD
Once you have been connected, find the user that you want to revoke the access tokens from, you can use the following command example to find the user:
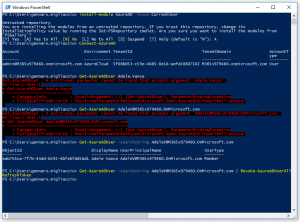
Get-AzureADUser -SearchString user@domain.com
Once you have confirmed the user, pipe this command into the revoke command. It will look something like this:
Get-AzureADUser -SearchString user@domain.com | Revoke-AzureADUserAllRefreshToken
The following image shows me running this against my demo tenant of Office365 for the user: Adele
Other Actions to Consider
As mentioned above, disable the user account while you run these actions This can be done from the Office365 Admin Portal User Management screen:
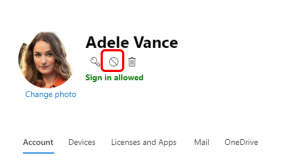
Blocking the user will remove the ability for them to login, this goes for the bad actor too.
After you have ran the disabling of the user and the revoking of the session tokens. It is then a good idea to change the user’s passwords, if you are using AD Connect with Password Sync, ensure that the password change has synced up before re-enabling the user account.
Enabling MFA if possible should also be an option, ensure that the user enrols into MFA (As if the attacker can still log in, then can enrol their own phone, rendering MFA useless). If you already have MFA enabled then it is worth checking the enrolled devices of the user to see if any additional devices have been setup (As the bad actor may of added a device or factor of their own). You can always force the user to re-register with MFA, however this needs to be done in the Azure AD Portal. Navigate to the ‘Users’ Section, select the User in question and then select ‘Authentication Methods’ to force a reset.
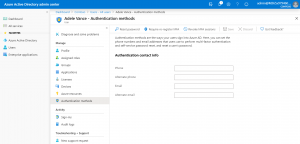
If the user account has any administrator access, then make sure these roles are removed, these can be reinstated when it is confirmed that the bad actor no longer has access to the account.
Do a quick check of mail rules, mailbox delegates and shared mailboxes that the user has access to in Exchange Online, look out for forwarding rules (as the bad actor might be siphoning data this way). It is also suggested to put the user mailbox in litigation hold so the emails are preserved. You can view and configure most of these options on the User Management Screen in Office365 Admin Center, under the ‘Mail’ tab. All other configuration will need to be done from Exchange Online Admin Center.
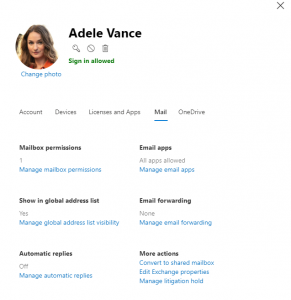
If the user has permissions to invite other users into SharePoint sites then make sure this is reviewed. The bad actor may have invited another account in to gain a further foothold.
Summary
While a shorter article then most of the others I have written, I hope this information proves to be useful should you find a compromised or even suspicious account. It is always worth reviewing the processes that you have internally to factor in steps like the above should an account be compromised so you have a structured way of investigating, containing and remediating breaches like this.
Additional things to also consider:
- Use Conditional Access to scope down access to resources based on conditions. Ie. User needs to log in from a corporate IP Address Range.
- Use Intune to further enhance the conditions in conditional access. Ie. User needs a corporate & compliant device to gain access to resources.
- Use Password Protection to ban certain passwords that might be easily guessable.
- Block legacy authentication and move toward using modern authentication for Office365 and Azure AD Apps.
Some of the above points however will require Azure Active Directory Premium, which is an additional cost to Office365. There is an article here that Microsoft has published with steps to increase identity security.
Please note that a number of Cyber attacks can be advanced and persistent. In all cases of a breach, I would always recommend you involve a forensic investigator to perform incident response. This way, you can ensure that the threat is contained and eradicated properly.
If you have any other methods, tricks or tips on how to deal with a compromised account, please feel free to comment!
Good article with good steps to take and how to prevent, keen to see more on the prevention side with MFA and associated technologies
Solid set of steps
Thanks Craig!