If you have had the privilege of administrating and configuring email systems and the security of email systems then you have probably come across the terms SPF, DKIM and DMARC. In this post i will talk a little around these three tools and their importance in email security.
Unfortunately, we are all familiar with spam mail messages that have constantly plagued user mailboxes, both personal and business. And since the start of the internet spam emails have only increased! Because of this we need to implement new technologies that combat spam messages, spoofing and general illegitimate emails…this is where SPF, DKIM and DMARC comes in.
SPF – Sender Policy Framework
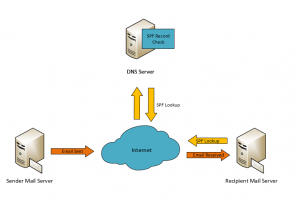
SPF, the Sender Policy Framework has been around for sometime. Its a technology that uses DNS to show a list of servers that are ‘allowed’ to send email for a specific domain.
You as an Administrator add text based DNS entries to DNS as SPF records which includes a list of IP Addresses and/or host names of Servers that are allowed to send emails. When you send an email to another domain, the recipient mail server will look up the senders domain against DNS’s SPF records to see if the source matches the host name or IPs listed.
Because SPF relies on an DNS entry, its reputable, as only admins that are allowed to change DNS settings for that domain can do so. The process of this is explained below (In simple terms):
- A SMTP HELO is initiated, the receiving mail server receives the HELO message and the sender addresses are obtained
- The receiving mail server runs a DNS Query against the senders domain and obtains the SPF Entries
- The SPF record is then used to verify the Sender Server, via either IP Address or Host-name
- If this matches, the mail is delivered to the recipient. Otherwise, the message is dropped and a rejection message is sent to the sender server
There are many spammers that spoof other businesses domains, and likewise there are products that use legitimate email spoofing to function (Salesforce, MailChimp, Printers ect.), in order to ensure these services are not marked as spam SPF records will need to be created for them.
DKIM – DomainKeys Identified Mail
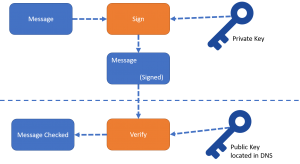
While SPF focuses on the message envelope, DKIM focuses on the message content and verifies that the content is trustworthy by validating its integrity.
DKIM uses asymmetric encryption (Public and Private Keys) to provide an additional layer of security and trust between the sender and the recipient. Similar to SPF, DKIM uses DNS entries. DNS is used to hold the public key for DKIM with the sender server signing the message with the private key. When the message reaches the recipient mail server the private key on the message is checked against the public keys in DNS to validate integrity of the message content. If the message content is modified during transit, the Public and Private key pair will not match and the message will be marked as non-trustworthy.
In the example below, i have attempted to illustrate the process as simple as possible.
DMARC – Domain based Message Authentication, Reporting & Conformance
DMARC, or Domain-based Message Authentication, Reporting and Conformance is a email validation process designed to detect and prevent spoof’ed emails.
DMARC is built on top of two existing anti-spam mechanisms, which we have detailed in this guide: SPF & DKIM. By using DMARC you can ensure that legitimate email is authenticated against DKIM and SPF standards, and emails that do not conform to these standards are blocked and reported on.
As we have established from the previous sections in the guide, SPF looks at the Email Envelope, while DKIM looks at the message content, by using DMARC you are effectively looking at both, as if the SPF and DKIM checks are not authenticated then the email will not pass DMARC. This makes DMARC an effective filtering solution against illegitimate emails and helps with the reduction of spam emails as well as spoofed emails.
The way that DMARC functions is when a mail server receives an inbound email, it uses DNS (Much like SPF and DKIM) to look up the published DMARC policy for the domain. The recipient server then evaluates the message for 3 key factors, these are:
- Did the message come from an IP Address Allowed list stated in the Sender SPF Record?
- Did the message pass validation of the DKIM Signature check?
- Does the message header show domain alignment?
The recipient server then applies the DMARC policy against the above information, and this will decide if the message is accepted, rejected or flagged/tagged. Once the DMARC policy is executes, the recipient mail server will produce a report detailing the outcome of the message and forward this to the sender domain.
The reporting aspect is one of the most powerful features of DMARC, as Mailbox providers can send DMARC reports to mail senders about which emails are authenticating and which emails are failing authentication and why, giving further insight and visibility into a mail system.
So why is DMARC so important? DMARC is used to reduce and mitigate email threats such as phishing scams as well as reduce the overall amount of spam sent to your organisation. DMARC also ties two known technologies together, providing a more robust method of detecting bad emails and enables specific defined actions to be taken dependent on the policies.
For more information on DMARC, please visit the official Website here: https://dmarc.org/
Thanks for reading! Please feel free to leave a comment below!
really nice thanks for share