Last Updated: 20/11/2024
So you’re interested in Hacking and Cracking? Or just want some free WiFi? Either way you have found the right place to start cracking WiFi.
Today we are going to walk through the steps needed to crack WiFi access points using a combination of wifite and Aircrack-ng. In this guide we will go through how to capture and crack the handshakes to reveal the WiFi Password.
What do I need?
Firstly, you will need a Kali machine! For the purpose of this guide I am using a vanilla install of Kali and am running all of my sessions and commands as a Root user. If you are using a standard account then ‘sudo’ will be required before most, if not all commands being executed.
My installation of Kali is on a Laptop with a compatible WiFi adapter which allows for monitor mode. This is necessary to capture packets ‘in the air’. A quick Google search will tell you which WiFi cards/adaptors are supported.
A good understanding of networking will certainly help for this. I would recommending looking into things like: Handshakes, WiFi Authentication, Deauth, Cracking concepts, Linux commands prior to attempting this.
Capture the Handshake
Boot up Kali and either navigate to ‘wifite‘ in the applications tab or open up a terminal and type in ‘wifite‘.
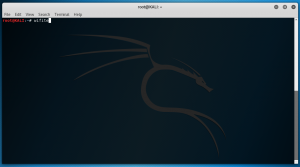
Immediately you will see a list of WiFi SSID’s begin to populate in the terminal window. The key thing to look out for is the amount of connected clients (as we are trying to capture a handshake between the client and the AP). The more clients, the better the chance of capturing.
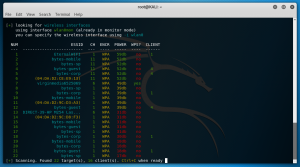
After choosing the Access Point in wifite, in this case ‘EternalWIFI’. It will attempt to deauth the clients connected (disconnect the Clients). Those clients will then try to re-establish a connection and in doing so, wifite will capture the initial handshake packets which contain the password hashes. The more clients that are connected to the AP the better the chance and more quicker wifite will capture the handshake packets.
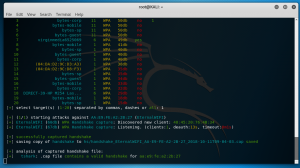
When a Handshake packet is captured, Wifite will try a default/simple password list. Its not bad and has worked for me a few times on individuals that tether phones and change their passwords to something very simple. You can of course edit this list to include more passwords.
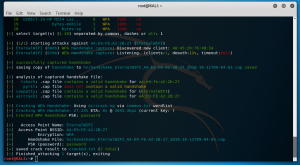
As you can see from the above, wifite has managed to crack the simple password which is ‘password’.
Password Lists
This however, will not always work. So we will need to crack the hash against a bigger password list. We are going to do this by using aircrack-ng. By feeding a password list against the captured handshake hash.
So, we are going to need passwords, lots of passwords!
If you need some password files I have zipped a few up HERE, I have found these on the Internet and take no credit for them!
However, the best way to get wordlists is by creating them yourself on Crunch. If you suspect that someone has changed their password to something ‘personal’ then it might be worth running CUPP (Common User Password Profiler) for a specific list.
Kali also comes with a default list (rockyou.txt) located in: /usr/share/wordlists
When cracking WiFi, the more you know about the network, router and users can help a lot. First things first would be to look at the SSID (most SSID’s have the brand of router included within the name) and this allows you to understand how many characters the default WiFi code is and the combination of letters, numbers, caps. An example of this is:
Default Iphone Hotspots/Tether will use 13 Lowercase only with Numbers (No Symbols or Caps). This information will allow us to filter our wordlists and create new wordlist around this.
Cracking the WiFi Handshake
Once you have downloaded or created a password list, it’s time to run this against the captured hash using aircrack-ng. The Syntax for aircrack-ng is:
aircrack-ng capturedpackets.cap -w wordlist.txt
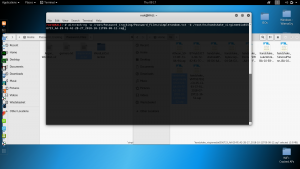
When we execute this, aircrack-ng will begin hashing the passwords from the list against the handshake password hash.
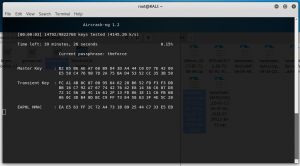
If the password is in the list then it will eventually strike a match.
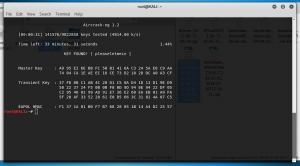
As you can see, the WiFi password is ‘pleaseletmein’. While a simple password, this one wasn’t in the common password file in wifite and required the use of our own wordlist in order to crack.
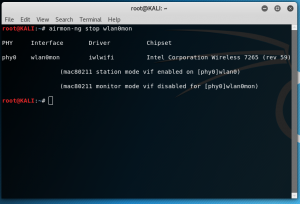
Exit Monitor Mode
Make sure you exit monitor mode on your WiFi adapter so you can test if the passphrase works.
The command for this is: airmon-ng stop wlan0mon
The interface could be different on your setup, so adjust accordingly.
Wrap up
So there we have it, a way of cracking WiFi. Please note that the cracking speed will be based upon your machines performance. It goes without saying that if the passphrase isn’t in your wordlist then you wont find the password. So make sure you build out specific wordlists dependent on the WiFi AP you want to crack. There are many other tools that you can use for the capture of the handshake and the cracking of the handshake. I prefer wifite as its easy to use and great for beginners and aircrack-ng has easy to remember syntax for piping a handshake to a wordlist.
Please use this knowledge responsibly and make sure you have consent to execute attacks such as this against someones Access Point. I take no responsibility for misuse of this information.
Please feel free to put any questions or comments in the section below.
Well written article, will try this when I next have a chance! Where can I get Kali and how is this installed?
Hi James,
Thanks for your feedback!
Kali can be downloaded here: https://www.kali.org/ I would recommend burning to USB with Rufus which can be downloaded for free here: https://rufus.ie/. If it gives you the option burn in DD mode not ISO mode as ISO mode can sometimes cause a few issues during installation. Hope this helps!
The link to your wordlists doesn’t work.
Thanks Korgan, I have updated the link and should be working now!
thank’s sir …nice article .. working on parrot
Thanks Kovic! Glad you liked the article 🙂
Thanks a lot for everything mate.
Your welcome Gothicboi, Thanks for reading!
Where can I get more wordlists?
Hi JDX!
For Wordlists that are tailored to a user, I have wrote the following article on using CUPP: https://gennaromigliaccio.com/common-user-password-profiler-cupp
However, for Wireless passwords I would recommend using Crunch to make wordlists. https://tools.kali.org/password-attacks/crunch
helpful
Thank you!
great article!
Thanks!
This Is A Really Great Article
Thank you!
thanks