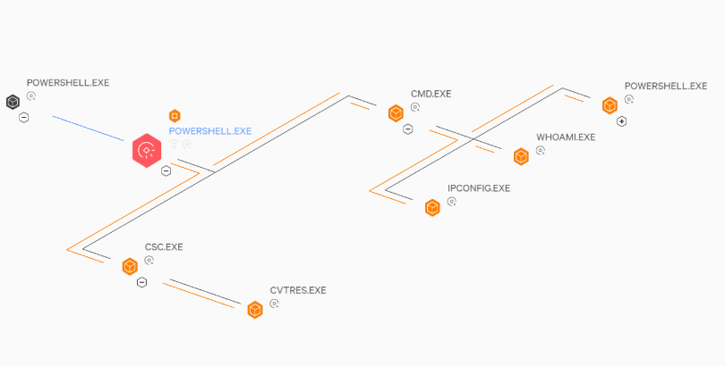
Lateral Movement Tactics and Techniques
In this article I am going to talk about some of the Tactics and Tools that attackers can use when they have intruded into your network. The list below isn’t a full and definitive list of methods, but does highlight some of the more common methods that are seen when moving through a network. Powershell […]