Last Updated: 03/10/2023
Introduction
We are all familiar with guest accounts in the broad sense that you can allow an external user in another tenancy to access files and services from within your tenancy. However, not many people know the options that you have in reverse, as in, how do we stop our users from becoming guests in other tenancies.
I have had this question asked to me a few times now, whereby the use case is literally to limit our users from accessing other resources in other tenancies in fear that this will act as a platform to leak and spill data.
So, if you want to limit your users from becoming guests in other tenancies, then read on.
Cross Tenant Access with Azure AD/Entra ID External Identities
To start off, this functionality/configuration is native to Azure AD. There is no third-party tool or solution that’s needed.
You can use Azure AD to configure cross-tenant access settings, this allows you to manage how your business collaborates with other Azure AD organisations. These settings let you configure how external Azure AD organisation collaborate with you (Inbound) and how your users collaborate with external Azure AD organisations (Outbound). For the purposes of this article, we will be focusing on the Outbound configuration.
Please note, that by default, Outbound access is configured to Allowed.
Step 1 – Discovery
First things first, it is highly recommended to first identify any outbound sign-ins to external tenants (Ie. Figure out if your users are accessing any other tenancy). Blocking access could block existing business-critical access to applications and stop users from working.
In order to find the user sign-in activity associated with external Azure AD Tenancies, you can use the following PowerShell script: https://github.com/AzureAD/MSIdentityTools/wiki/Get-MSIDCrossTenantAccessActivity be sure to use this with the: -SummaryStats and -ResolveTenantID switches, as well as the -AccessDirection Outbound parameter.
Example 7 in the github page outlines the correct command to use:
Get-MsIdCrossTenantAccessActivity -AccessDirection Outbound -SummaryStats -ResolveTenantId
This will produce an output that will list out the sign-ins for local users accessing resources in external tenancies, it will also list out the external tenant GUID and attempt to resolve this into the tenancy name.
Step 2 – Control Cross-Tenant Access
Once you have confirmed that user impact will not be affected, you can then proceed to making the change. To do this, log into Azure AD with Global Administrator Access. https://aad.portal.azure.com/. Navigate to: Microsoft Entra ID > External Identities > Cross-tenant access settings.
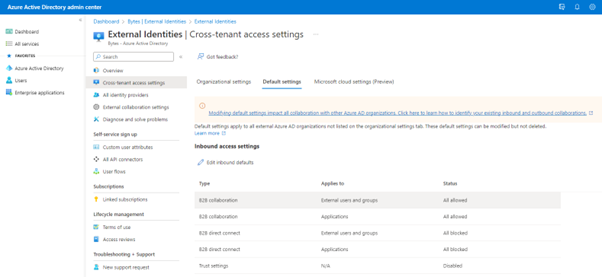
Locate the “Outbound Access Settings” and click on edit.
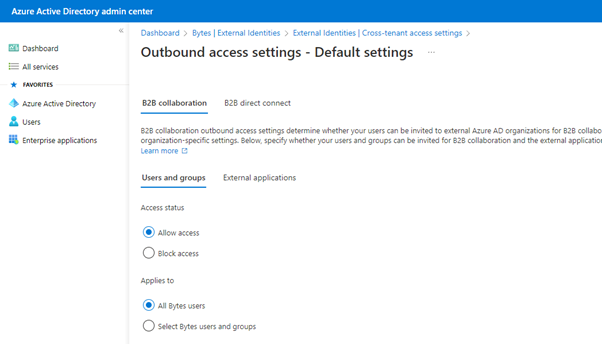
Summary
Whilst not a comprehensive guide to Azure AD External Identities, this should hopefully provide the guidance and validation needed that your users can be restricted from accessing other tenancies. There are more options available in the Cross-tenant access settings which allow for exceptions to be made to listed organisations, effectively giving you an “allow list” method of adding only authorised/approved tenancies.
Thank you for reading!