DevSecOps with Sophos Cloud Optix
Introduction
Welcome to another article about Sophos Cloud Optix, while my last article (Which can be found here) took a focus on how to secure your IaaS environments and gaining visibility over resources, this article is going to take a similar focus, but on the DevSecOps side. This article will go through how Sophos Cloud Optix can plug into an IaC (Infrastructure as Code) environment to determine compliance, as well as feeding this back into the development process.
To put some meat around the bone, it’s worth starting off with the difference between DevOps and DevSecOps, as knowing the difference between these really provides the context on how something like Sophos Cloud Optix shows its value.
DevOps and DevSecOps
DevOps combines software development and operations to shorten the development lifecycle of an application or project, it enables developers to code operate on a scalable and usable platform. Some of the key components and upcoming areas of DevOps that we have seen are things like Infrastructure as Code (IaC) that allows us to deploy resources as code. In other words, using scripts to build applications and services, here we have a developer centric approach to IT Operations! This sounds great; however, the issue is that security is left out of this process completely or is sometimes only considered at the end of the development lifecycle. DevOps also go through continuous change; code is being updated on a regular basis to improve the application and these changes impact the security posture at every release.
As we all know, the rate of change with developing applications is very high, yet many security and compliance monitoring tools and methodologies haven’t kept up with this rate of change, as they were not built to test code at the speed we are used to in DevOps. This then creates a perception that security is a roadblock to rapid application development.
This is where DevSecOps comes into play, DevSecOps simple incorporates security as part of the DevOps process, and ensures continuous monitoring over the code even throughout changes.
By monitoring and assessing the code and any subsequent changes throughout the lifecycle ensures the applications and services being delivered are secure and are not leaving services vulnerable. As most exploits will be based upon faulty coding.
We have all seen cases were an IaC template has been deployed that has security and compliance misconfigurations that can end up leaving services and data exposed, if that insecure IaC template isn’t identified before its deployed then it could open multiple services to exploitation.
Using Cloud Optix to achieve DevSecOps
So, where does Sophos Cloud Optix come in? You would have seen in my previous article that I wrote about Sophos Cloud Optix from the perspective of deploying resource into AWS, Azure and GCP. However, this is based on resources already deployed in the cloud, they were not deployed from an ongoing code repo. If they were, then the applications and services would only be scanned AFTER they are deployed. This doesn’t help us much if what we are ABOUT to deploy is vulnerable and full of security flaws. Realistically, we need a solution to scan and assess the code BEFORE we deploy into a cloud environment and ensure that’s is secure and aligned to best practices.
Sophos Cloud Optix can do exactly that, it can integrate into the DevOps process and perform a Security and Compliance Assessment against the code while it’s in staging (Before deployment) and located in Source Control Management (SCM) rather than fully deployed and live.
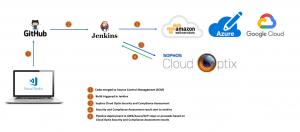
This results in a more secure approach to deploying applications and services into cloud services.
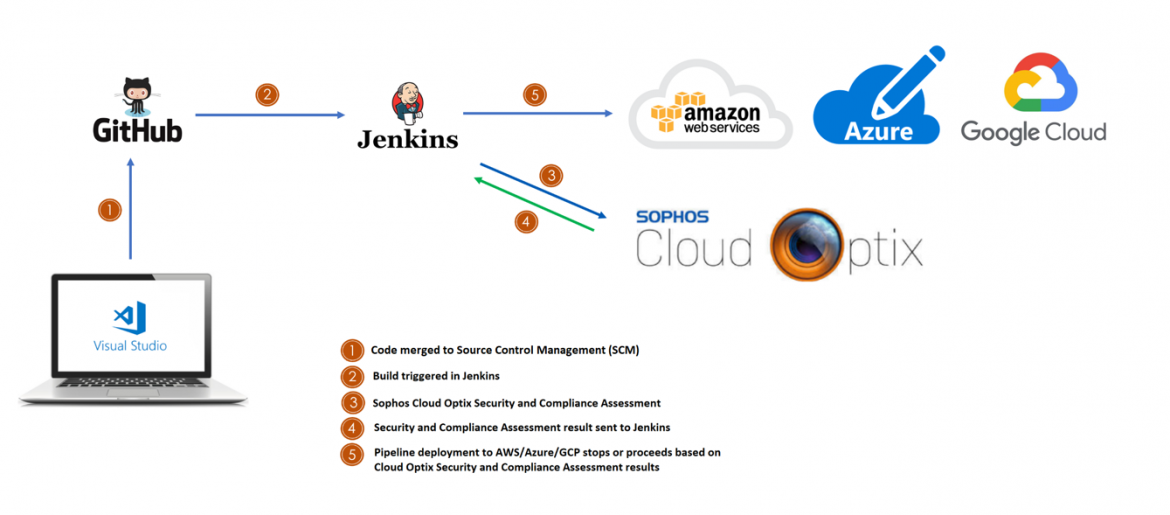
Sophos Cloud Optix can integrate into Source Control Management (SCM) such as GitHub and pull the code in for assessment, this assessment will identify areas where best practices are not met and provide recommendations on how to remediate these. However, to make the process even smoother, Cloud Optix can also integrate into Continuous Integration (CI) services such as Jenkins to halt or progress the pipeline deployment of the code in question. This seamless integration into the workflow allows for minimal impact on developer timelines but still maintains an adequate level of security.
In a use case like this, only code that has passed and been validated by Sophos Cloud Optix will be deployed out, this is useful for when updates need to be made to an existing system. When updates to code are made this can sometimes open other areas to security vulnerability. By integrating Sophos Cloud Optix into the development pipeline itself, we can mitigate these vulnerabilities and ensure that the application and service updates that are being made are indeed secure.
Sophos Cloud Optix supports integration into various SCM’s and CI’s. Below is a screenshot of some of the integrations that Sophos Cloud Optix supports:
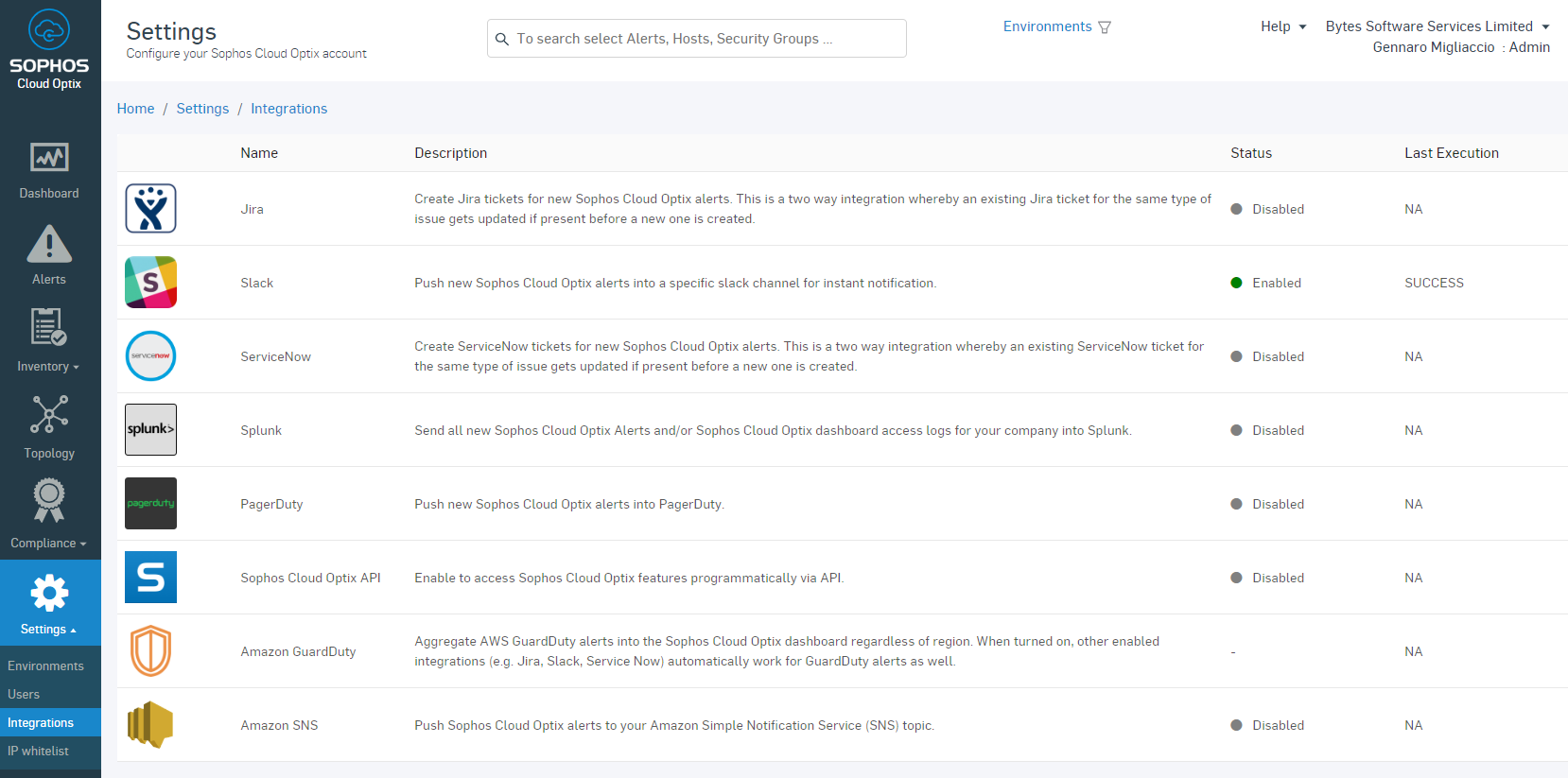
As for the supported IaC environments, the following SCM providers are supported:
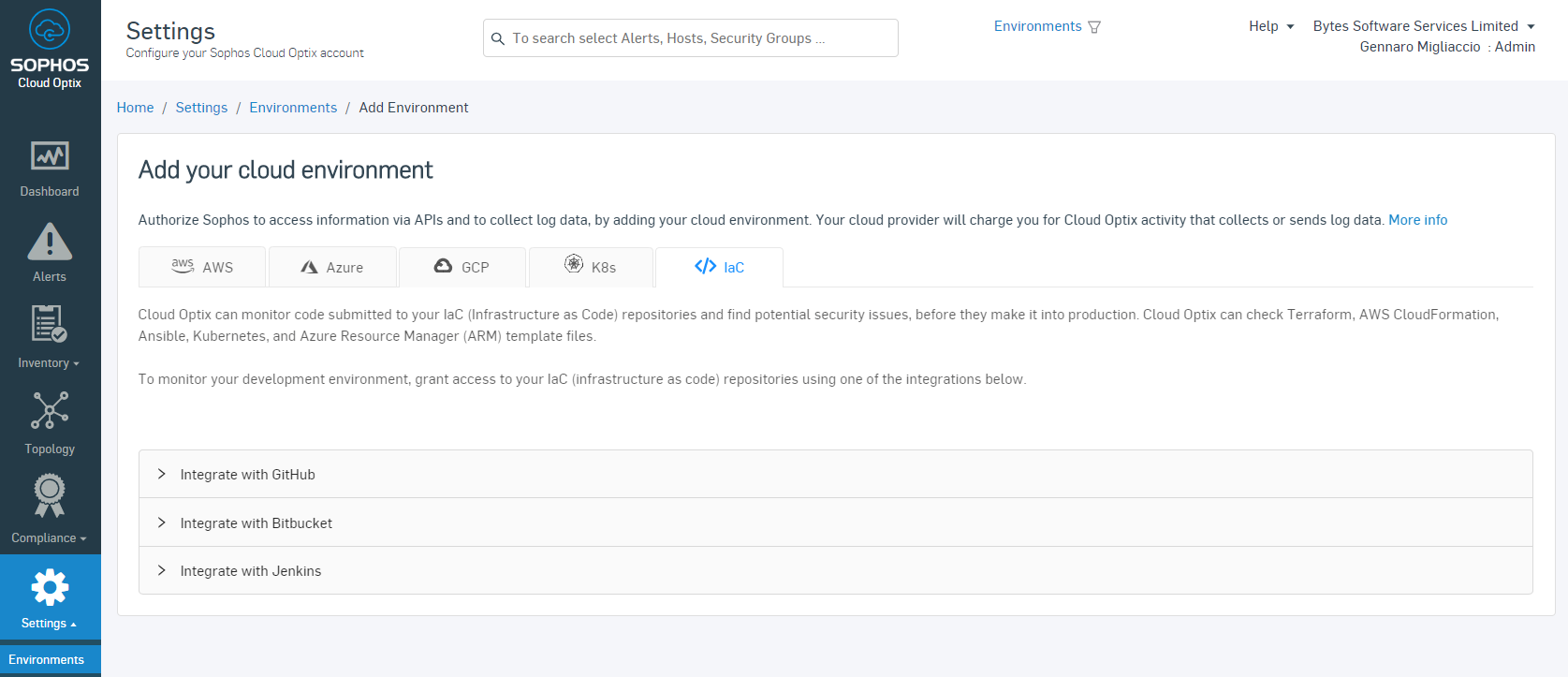
How does this look in Cloud Optix?
The below screen clip shows some of the alerts that Sophos Cloud Optix can generate when connected into an IaC environment.
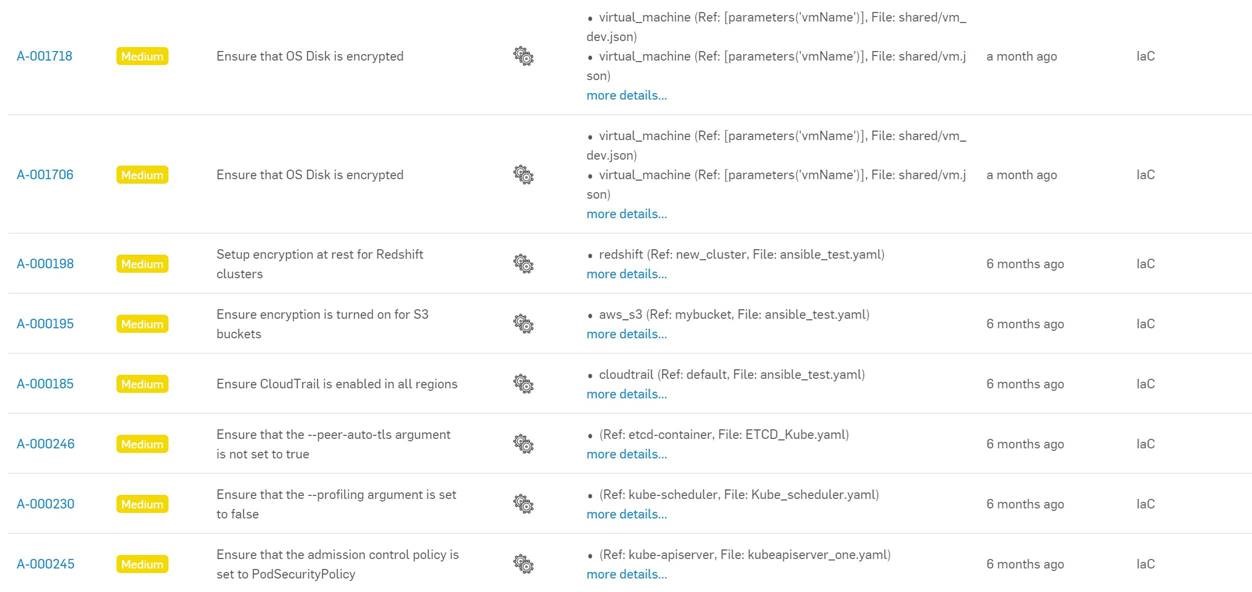
Sophos can detect abnormalities with code, as if they are already deployed as resources, therefore we are able to see some abnormalities such as if Storage Accounts, S3 Buckets and disks are encrypted.
Like the last article I wrote on Sophos Cloud Optix, you have the capability to go into these alerts where it will specify the affected resources and give high level guidance on remediation. This is great for pinpointing issues and feeding back to the development team before an application or script is pushed through to production.
In terms of what Sophos Cloud Optix can identify, there are several different policies that can be enabled when assessing an IaC environment or repo. By navigating to the custom policies section of Sophos Cloud Optix we can see the different configurations that Sophos Cloud Optix is looking for regarding IaC configurations. I have put a screen clip of some of the rules below, however its worth noting that Sophos Cloud Optix has about 200 rules for the IaC Assessment.
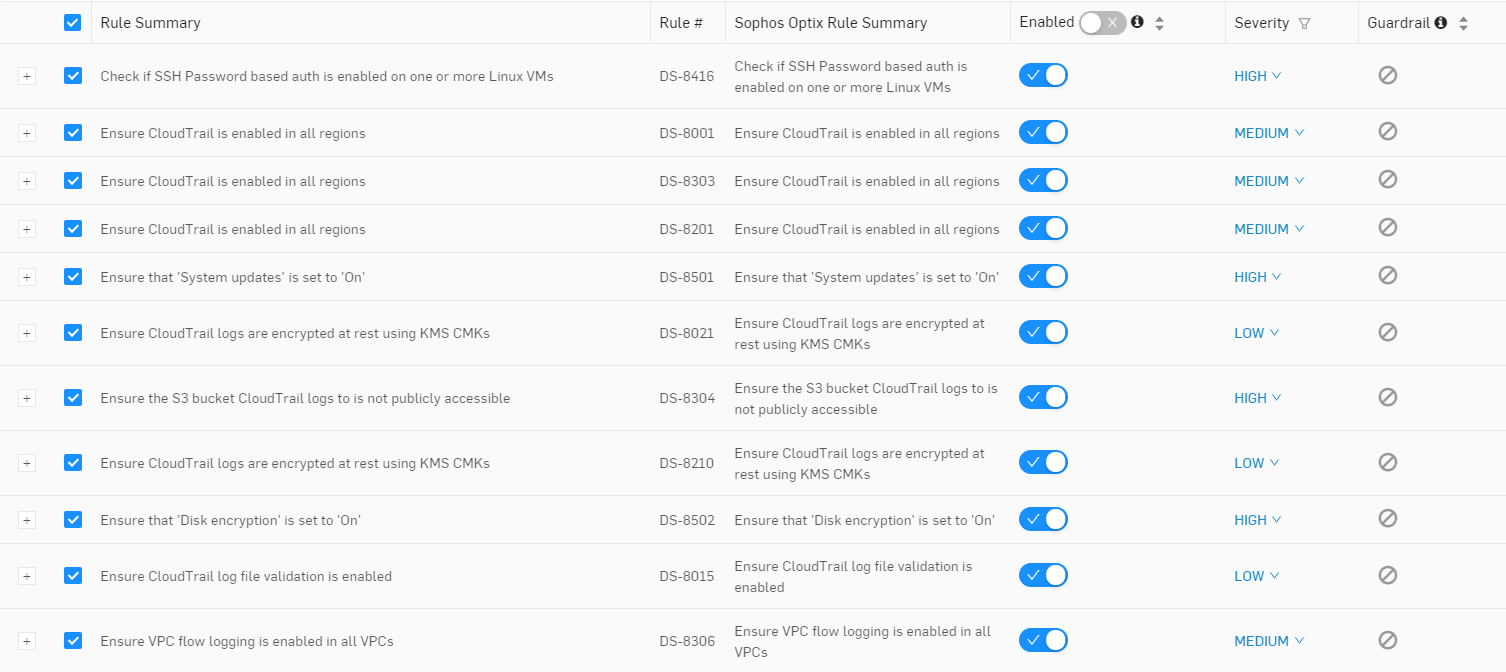
Summary
Sophos Cloud Optix provides the next step that takes DevOps to DevSecOps, it allows for a natural integration into the Software Development Lifecycle to provide valuable insights over how resources are coded and created, this can then feedback into the pipeline process to ensure that what is being published and deployed is secure and fit for purpose, mitigating security exploits and remaining compliant. Seeing as Sophos Cloud Optix can already view IaaS based resources that are deployed, it fits nicely to get a view of resources that are yet to be deployed. Giving a tremendous amount of visibility into security and compliance of cloud resources.
This blog only shows a partial view into the full capability with Sophos Cloud Optix. As always, its recommended to get your hands on a copy and test this yourself! Sophos Cloud Optix can be trialed for 30 days, giving enough time for you to test its capabilities against your own GitHub Repos and perform an assessment of the current code. For an ongoing assessment of your code and integrating this long term into your development pipeline, Sophos Cloud Optix should be considered as a tool to accomplish this.
As mentioned above, A trial can be provisioned of Sophos Cloud Optix here. If you want to see the alerts in action, then you can clone some sample insecure templates created by the Sophos team here. These templates are for testing only, and provide a good method to see what Sophos Cloud Optix can detect.
Good Post! Explains the Devsecops piece very well
Thanks Matt!